Attributes
- Author(s): @addison @pierre
- Parameter: MaxValidators
- Current Value: 1000
- New Value: 5000 (over a period of 1 month)
Summary
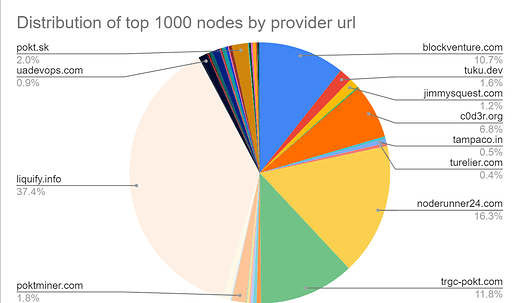
Right now the amount of pocket needed to take over the network is extremely low. The top 1000 validators have 19.8m pokt staked. This means that an attacker would need 13m pocket in order to take complete control of the network. At current prices, this is $2.6m USD, which is a very small amount for a network of this size. We should increase the MaxValidators parameter in order to improve the economic security of the network. I propose we increase the parameter to 5000 over a period of 1 month, which would increase the validator stake total to 81m and amount required to attack the network to 54m POKT/ $10.8m USD.
Abstract
The MaxValidators parameter determines how many of the top nodes by stake are considerd validators. Currently the value is quite low and needs to be increased.
View current validator distribution here:
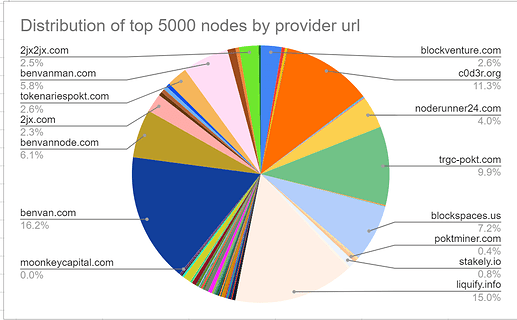
View desired validator distribution at 5k validators here:
Motivation
This parameter change would increase the network security from 13m pokt ($2.6m USD) to 54m pokt ($10.8m USD) and further mitigate attackers and malicious actors.
Rationale
We cannot have a $300m protocol that peaked at $2.5b secured by $5m of assets. Here are a few of the many possible threats if someone were to get 66% of the validation power.
- Chain halt
The chain could shut down. Apps would stop receiving service and nobody would be able to transfer POKT - Exchange/OTC reorg
Someone could deposit pocket onto the exchanges at block N, market sell and take all of the buy liquidity. After this, they could produce another block off of block N-1, orphaning block N and returning all of their funds - Modify consensus
Someone would be able to modify consensus and pretty much do whatever they wanted.
5k is not a firm selection and can be modified. Please see this sheet for analysis and charts to determine the optimal value for yourself. We should try to determine a value that increases the economic security while reducing overhead on node runners and the state. Core devs can chime in here to provide insight into the implications of increasing the validator count.
We could also consider pursuing an approach where the MaxValidators parameter is continously adjusted so that the validator stake always equals a certain threshold.
Implementation
Per Jack’s insight, we should increase the validator count steadily.
I propose we increase the validator count as Jack said upon the following timeline. The foundation will handle the parameter changes.
Upon Passing: 1500
Week 1: 2250
Week 2: 3375
Week 3: 5000
This will allow us to observe changes and ensure the network remains healthy.
Dissenting Opinions
- This will cause too much chain bloat.
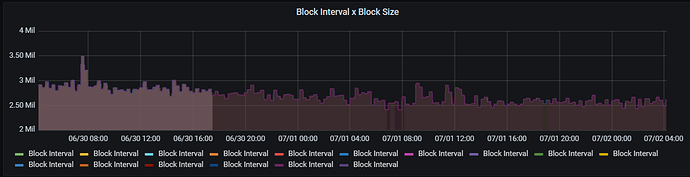
The max blocksize is 4mb. Currently blocks are about 2.6 mb. This change would increase blocksizes by .9mb according to Andrew’s post. This would be approximately 2.5gb a month. This is definitely worth it in order to ensure we have a secure network.
The following is a chart of blocksize in the past 2 days.
If we increased blocks by .9mb, this would put blocks at around 3.5mb, which allots for some spikes.
- Pocket is illiquid. Nobody could acquire this much pocket.
There are individuals with this much pocket and from my experience running the OTC, I have no doubt that someone would be able to acquire 13m POKT with decent slippage.
- There is no economic incentive for someone to attack the network.
Regardless of someone’s incentive, we need to ensure that the network is economically secure. A competitor could see this as an opportunity to end pocket, we cannot have this liability. Also, regardless of the risk of an attacker, the validator set needs to be diversified. Liquify currenty has 37.5% of the validator power. What happens if they go offline due to a bug in their infrastructure?
- We should instead further incentivize validators instead of changing this parameter.
That would be a more significant change and require greater thought as that would affect everyone in the ecosystem. This is a seemingly easy change that would drastically improve network security.
- The DAO, foundation and other whales would be able to step in if an attacker arose.
This is not a suitable defense. There are no alerting systems currently for validator stake. It would also be a massive coordination effort in order for the DAO or other people to combine funds and stake it ont o a validator. They might not be able to react quick enough as the aforementioned threats only require a block or two to occur.
Analyst(s)
See analysis here
Thank you to poktscan for the raw data.
Copyright
Copyright and related rights waived via CC0.