Hi @Jinx
Thanks for your feedback.
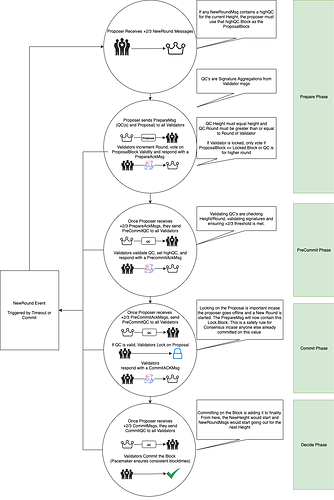
Let me address the issue of consensus breaking or not. What @FerrumNetwork (Nick Odio) mentioned in the Telegram message referenced in your picture was referring to the fact that the following areas of the consensus protocol will not be impacted:
Reference
Pocket contribution guide defines consensus breaking changes as follows:
Consensus-breaking changes
A consensus-breaking change means a change that would require 66% of the Validator Power in the network to be adopted. Furthermore these changes need to be voted in and approved by the DAO. To propose a consensus-breaking change please follow the Pocket Improvement Proposal documentation found here.
Your key question was:
Is this going to be a consensus breaking change or not?
The nature of the update will actually require an update to the core as it is proposed and implemented. Hence, according to the definition described in the Pocket Contribution guide, it will in fact be a consensus-breaking change.
To be clear Nick was sharing information he had been provided so this is not on him, we need to improve in this area as you can see we are making an effort to improve direct communication with the community.
In this case, it appears that upon discovering that difficulty, the Ferrum team perhaps made an initial effort at notifying the Pocket core team, which was understaffed at the time, and then…did nothing? For months?
There’s simply been a year of intermittent activity on a series of repos which suddenly ramped up in the last two months
This is not the case. When we discovered the adjustment in scope, we had to make updates both on the Ferrum Node Infrastructure side and client side in addition to changes to core and wallet client.
Please review:
https://ferrumnetwork.atlassian.net/wiki/spaces/FN/blog/2021/12/23/329941007/Connecting+EVM+to+the+Rest+of+the+World+Phase+1
https://ferrumnetwork.atlassian.net/wiki/spaces/FN/blog/2022/02/08/334102548/POKT+wPOKT+and+Ferrum+Network+Token+Bridge+Integration+Update
Also review forked repos by our engineers or you can review the PRs when they are created.
While I’ve been excited about the potential of wpokt (for all of the reasons outlined in my RFP-11: A Bridge To The Future post), the risk to reward ratio of continuing down the current path has flipped in favor of waiting to see what sort of native on-chain mechanisms (such as an IBC integration) can be implemented in v1.
Per my latest conversation with the Pocket Network team, while there isn’t a defined timeline around v1, it’s currently scheduled to start roll-out around Q3/Q4 of 2023. This could be delayed as is the case with any complex undertaking.
Given that Ferrum will take on the technical debt and burden for the changes requested, regression testing, performance impact reports, and Alpha testing. I don’t see how it has more than a low-to-moderate impact to the network. I’m sure there will be updates between now and v1 and this update can be included along with it. We will make sure to incorporate and satisfy the community, PNI and DAOs concerns before the PR is actually considered for merge and rollout to BETA.
Not launching this bridge means:
- Giving up on nearly a years worth of effort
- Delaying POKT / wPOKT interoperability for potentially another 24 months+
Hi @Cryptocorn
Thanks for your feedback. I’ll share some responses to your questions. I see that others have also raised a few questions regarding our team and staffing. I’ll share responses to all those posts in this response.
We seem to have a strategy officer as acting CEO/CTO
I believe you are referring to me here. I started off as an investor in the organization, joined the GC, and eventually came on board full-time as the Chief Strategy Officer at Ferrum. I am an engineer by background and have served organizations as Chief Software Architect and CTO for a good part of the decade. I have taken over CTO responsibilities in the last quarter.
Project Manager running an external team
I believe you are referring to the staffing agency we use. All Ferrum team members are full-time employees. Due to our incorporation jurisdiction, and local regulations, benefits administration among other things we work through staffing agencies where we cannot directly employ team members. Regardless of the entity that manages payroll, benefits globally, 95%+ of the Ferrum team are full-time team members.
Ferrum haven’t answered my questions in the past
@Cryptocorn please post your questions here and I’ll answer them
Can you name your: (@Sandy410 @Joe018 )
CEO: Naiem Yeganeh
CTO/CSO: Taha Abbasi
COO: Ian Friend
CGO: Nick Odio
Are they full-time employees of Ferrum or outsourced?
All of the team members mentioned above, along with the entire dev team is full-time Ferrum team members.
Yeah, this stinks of being a shady two man operation (Taha + Nick) who outsources all the work to Pakistan. All the tech leads named on the call work for a 3rd party BPO, not Ferrum.
@Harvey007 guys, can we keep this civil and focused on actual feedback/questions about the project and proposed changes? There really isn’t a need to be uncivil.
Wow, these guys are dodgy, just trying to milk the DAO for more money while demoing basic stuff.
If the community hasn’t seen it, Taha looks like a known swindler:
@Zack-Ackerman Really?
- This PIP is not asking for more funds. It’s just a request for feedback and suggested changes so Ferrum can continue to invest in this integration and in the success of Pocket Network.
- This occurred when I learned that my name and credentials were being used by that company’s founder to raise funds from investors and the money raised was being embezzled. Employees weren’t being paid, bills weren’t being paid, etc. I brought up the issue internally and requested the practices to stop.
Long story short, I was let go as I didn’t get with the program and this followed along with a cease and desist to try to keep me quiet. You can review the details of the lawsuit here.
Here is some more info that might help.
The CEO of Tryp deployed a defamation campaign to try to stop me from reporting him to the authorities. This is explained in the lawsuit. The guy was embezzling money and not paying employees.
The content of these blogs is completely fabricated and immensely defamatory.
I asked my colleagues who “supposedly” wrote those blogs for comment, each one of them completely denied these claims. They were appalled at the content being shared and how I was being misrepresented.
I asked my colleagues for their video testimonials.
-
CEO of Evelar
-
CRO of Evelar
-
Board Member and Co-Founder at SimuStream
My request for testimony
https://www.videoask.com/fv0eoanhu
Their responses:
https://www.videoask.com/rjkkxu9jhihon43lnt3hlopuhg39j2jh864s0a9l
Important Note and Clarification
I’m excited to review the feedback shared here with our team and come back with updates to the PIP…
I want to clarify one thing, this is not a request for additional funds. Just for feedback and to answer questions and make adjustments in a public forum. Also, there were mentions of Ferrum trying to put the blame on the Pocket team. We are in no way trying to put any blame on Pocket Network team or point fingers. In fact, we are thankful for the support they have provided thus far.
We truly appreciate the accountability and thoughtfulness the community is bringing to the table. We’re committed to getting this done correctly and won’t give up. We’ve got some homework, we’ll get right to it.
A note, in the US Monday is a holiday, so some of our responses might not come until Tuesday / Wednesday.